Written by Marten Cureton – Technical Pre-Sales Lead
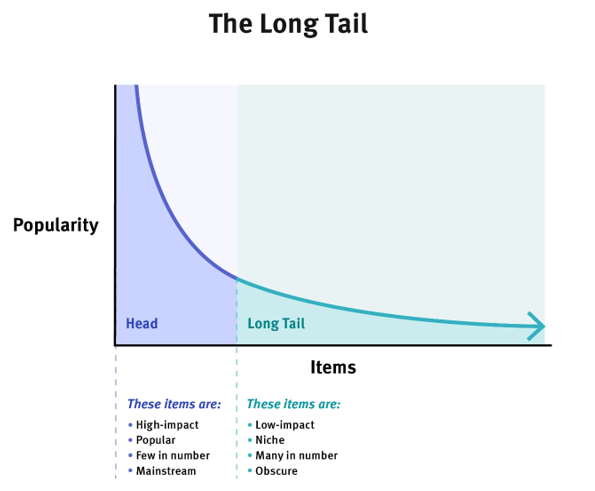
Long tail data is often synonymous with Data Science and the distribution of data based on the number of aggregated data points. However, as for any organisation, information is vital and long tail data can often be overlooked due to the overall impact this data typically has when compared to high-impact, high-volume data – as shown in the image below.
But, if we were to consider long tail data in the context of Cyber Security, we have the reverse.
Low-impact data can become high-impact outcomes for a Threat Actor and it is often the case that attackers take the “low and slow” approach to operating within a corporate network. So, if we have an organisation whose focus is only on high-impact information, it is likely the Threat Actor will succeed in their objective of remaining undetected.
In Cyber Security, analysing long tail data can tell us a lot about what is happening at the lower end of the scale. The image above shows that this data is typically obscure or niche and therefore can add value should it be exploited at the right moment. The same can be said for a Threat Actor looking to achieve a certain goal within the network, it is just a matter of perspective.
Detecting these possible breaches within long tail data can be onerous, as this type of data is often high in volume with each data point being unique and therefore the longer it is left, the harder it is to find anomalous behaviour.
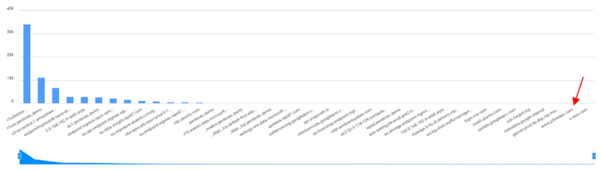
Selecting the correct approach and tooling will enable the security team to analyse this type of data on a regular basis and carefully selecting the right queries to search through that data will significantly reduce the time it takes to identify obscure traffic, such as a spoofed domain, as shown in the image below.
As you can see, high-volume data could very easily overshadow a small handful of connections to a spoofed domain and therefore it is vital that security teams and businesses are aware of the dangers of not paying attention to data like this. It’s often the case that teams or security tools are only looking for the low-hanging fruit.
However, here at Pentesec, we offer several Managed Security Services that are backed by our expert team of Security Analysts who are all too aware of such dangers. We take a proactive approach to analysing long tail data and, between the people and technologies we employ, we can protect our customers from threats that could be hiding within your IT infrastructure.
Services that can help:
Managed SIEM
Built by experts, Security Essentials provides instant visibility into your users, devices and attackers and offers deeper insight into the threats you face, alerting you to risks in your environment and providing immediate value to your organisation.
Our team can monitor your network activity and alert you immediately whenever there is a risk that needs your attention – leaving you to focus on everything else that matters to your business.
Managed Detection and Response
Our MDR service provides state of the art, real-time continuous monitoring and active threat prevention across customer endpoints.
We take telemetry from other key customer security systems and use it to enhance visibility of potential threats and compromises while reducing the mean time to respond (MTTR).