In an era where attacks are increasingly more sophisticated, it is critical that the defensive capabilities you employ can collect, assemble, and interpret the data flowing through your network.
These data fragments are the building blocks of intelligence that form early warning signs that your network may be under attack and being able to identify these vital warning signs can dramatically decrease the Mean-Time-To-Mitigation (MTTM).
Indicators of Attack (IOA) are the very pieces of information that turn a reactive defence, into a proactive defence.
Indicators of Compromise (IOC) is a phrase that has become synonymous with cyber security; however, they typically only provide evidence that your network has been the subject of a previous attack, meaning the information is reactive evidence.
Conversely, IOA’s look at alerting us to an attack, based on known or emerging attacker techniques, as they unfold and can be considered proactive evidence that spans all phases of an attack.
This means IOCs are static events while IOA’s are emerging events.
Let’s look at an example:
We know our neighbour is selling their car and, as a result, it could be considered normal to see strangers looking through the car window before knocking on the door.
However, if we know that our neighbour isn’t selling their car and they are on holiday, but the same situation occurs, we take a different perspective and may challenge that person before they are able to commit a crime. The same can be said for cyber security.
Here at Pentesec, we adopt the proactive approach to cyber defence and that starts with the technology stack we have carefully chosen so that we can reduce the MTTM.
If we take a cyber-related scenario where an attacker is openly attempting to exploit a known vulnerability based on Log4Shell with the intent to deliver Ransomware, our chosen technology can identify the IOAs, from Reconnaissance to Payload Execution and trigger an action that enables our analysts to identify the risks and mitigate the attack from achieving its objective.
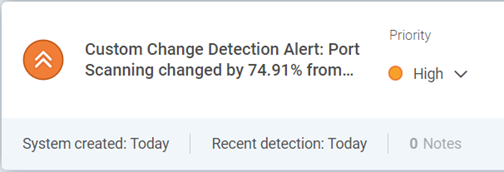
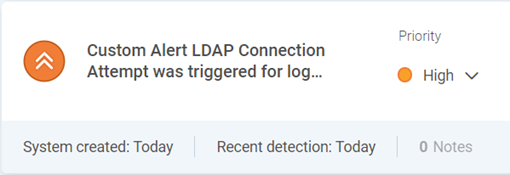
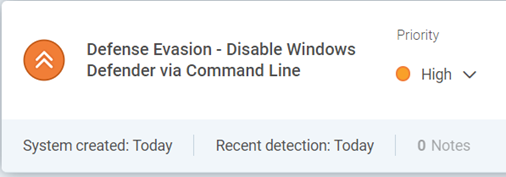
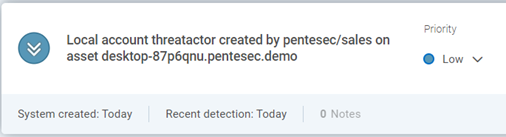
The images below are based on the previously described scenario, against Rapid7’s InsightIDR and our EDR tool from SentinelOne, and our ability to identify the attack as it unfolds.
Reconnaisance – Analyst is alerted by a custom threshold rule to detect port scanning
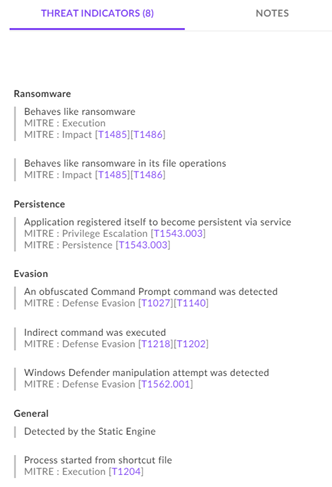
Initial Access – Log4Shell IOA detected by custom LDAP connection rule to external IP addresses
Defence Evasion – Rapid7 detects next IOA as attacker attempts to remotely disable the anti-virus to evade detection
Persistence – Local account is created as an IOA for possible secondary credential access
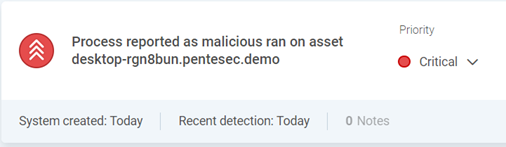
Execution – Upon successful delivery of the ransomware, the payload is executed
Mitigated – Finally, the threat is mitigated by SentinelOne
While scenarios such as these are not uncommon, detecting IOAs early in the attack chain as shown can avoid the harm that can arise from a threat actor achieving their objective, in this case, the delivery of ransomware, one of the top threats to organisations today.
If you’d like to find out more about our approach to proactive defence, or about any of our Managed Security Services, please contact us on 0845 519 1337 or email enquiries@pentesec.